The CHFI: Certified Hacking Forensic Investigator training course is a completely ANSI-accredited and lab-focused program. This CHFI training is vendor-neutral training in digital forensics.
Courses
Experience
Global Learners
The CHFI: Certified Hacking Forensic Investigator training course is a completely ANSI-accredited and lab-focused program.
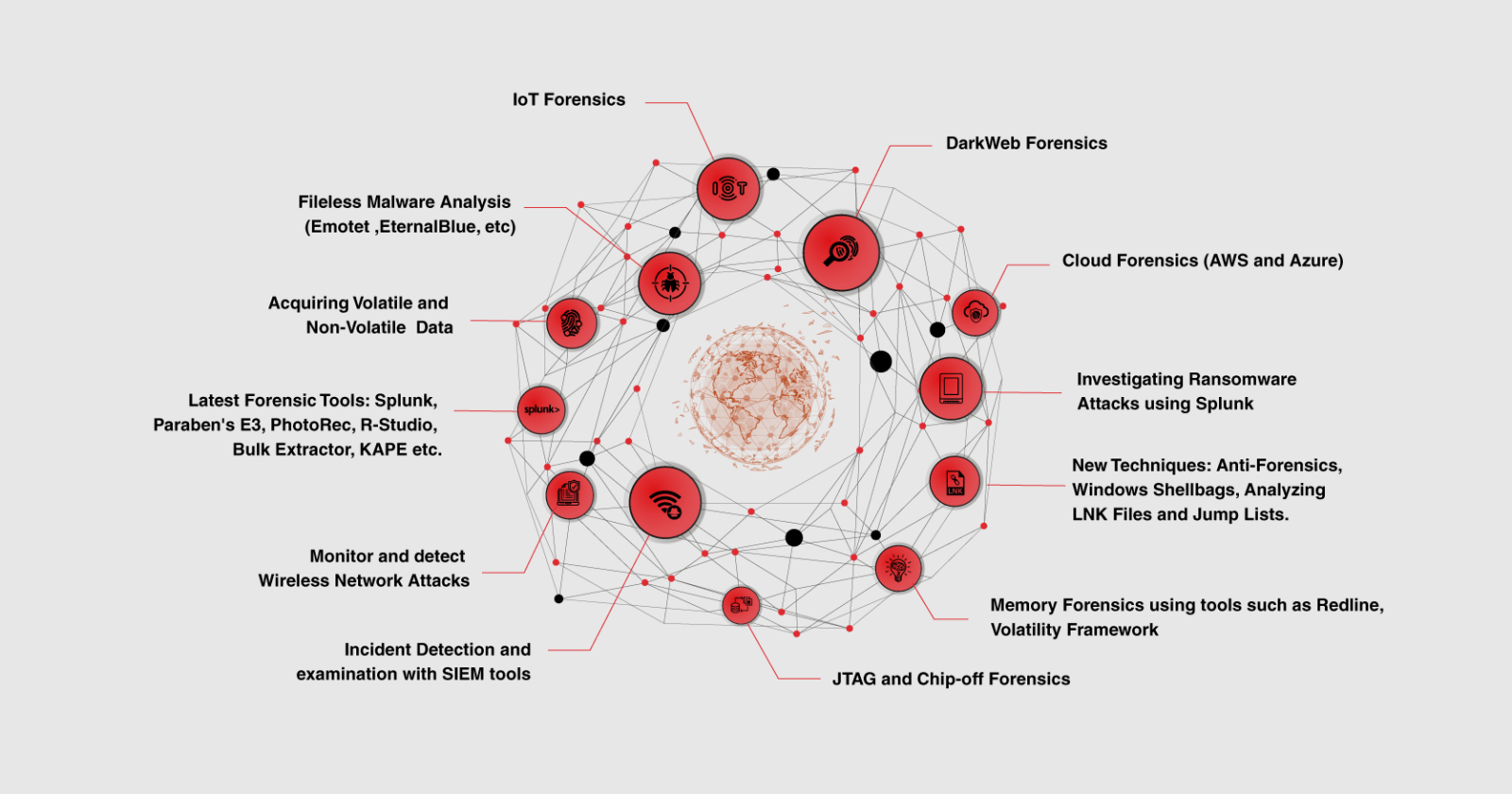
This CHFI training is vendor-neutral training in digital forensics. With this training, the participant will understand digital forensics, the detailed and best approach to digital forensics, and evidence analysis that revolves around Dark Web, IoT, and Cloud Forensics.
With the help of techniques and tools, the participant will learn to conduct digital investigations and groundbreaking digital forensics technologies.
This Certified Hacking Forensic Investigator training program is for IT professionals involved with information system security, computer forensics, and incident response.
It helps strengthen the application knowledge in digital forensics for forensic analysts, cybercrime investigators, cyber defense forensic analysts, incident responders, information technology auditors, malware analysts, security consultants, and chief security officers.
The CHFI training provides the essential skills to proactively investigate complicated security threats, allowing them to explore, record, and report cybercrimes to prevent future attacks.
Click here to download CHFI Battle Card
Note: This training is DOD-approved (DEPARTMENT OF DEFENSE)
|
|
|
|
|
|
|
|
Reach out to our learning advisors for personalized guidance on choosing the right course, group training, or enterprise packages.
📞 Talk to an AdvisorFor over 10 years, Microtek Learning has helped organizations, leaders, students and professionals to reach their maximum potential. We have led the path by addressing their challenges and advancing their performances.














Microsoft Learning
Partner of the Year

5000 List of the Fastest-Growing Private Companies in America

Top IT Training Companies
(Multiple Years)

Our expert counseling team provides round-the-clock assistance with the best value offers.

Certified trainers with 5–15 years of real-world industry experience guide your learning.

We guarantee satisfaction with top-quality content and instructor delivery.

Train with industry projects and curricula aligned to current standards.

We promise the lowest pricing and best offers in the market.

All courses are assured to run on scheduled dates via all delivery methods.
Explore our collection of free resources to boost your EC-Council learning journey