
Cybersecurity is one of the most important aspects of any company at this point, with the growing prowess of cybercriminals. With the world being digitally dependent, protecting data is top of the priority list for any organization. According to reports, Cybersecurity Ventures predict a growth of global cybercrime by 15%. This would lead to $10.5 Trillion USD annually by 2025. Cybersecurity is no longer an optional criterion for any organization. Keeping the protection of data as the top priority, obtaining an ISO/IEC 27001 certification is one of the most effective ways to strengthen cybersecurity.
By the end of this blog, you will know how one can gain ISO/IEC certification, along with all the necessary insights into this certification. Without further adieu, let’s dive into the matter, shall we?
| Explore ISO/IEC 27001 Certifications |
|---|
| ISO/IEC 27001 Foundation ISO/IEC 27001: 2022 Lead Implementer ISO/IEC 27001: 2022 Lead Auditor ISO/IEC 27001 Transition Training |
What exactly is ISO/IEC 27001?
ISO/IEC 27001 is an internationally recognized standard for managing information security. This certification provides a systematic approach for securing sensitive company data while ensuring confidentiality, integrity, and availability of the information. Created by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), this standard sets out the specifications for creating an effective Information Security Management System (ISMS).
History
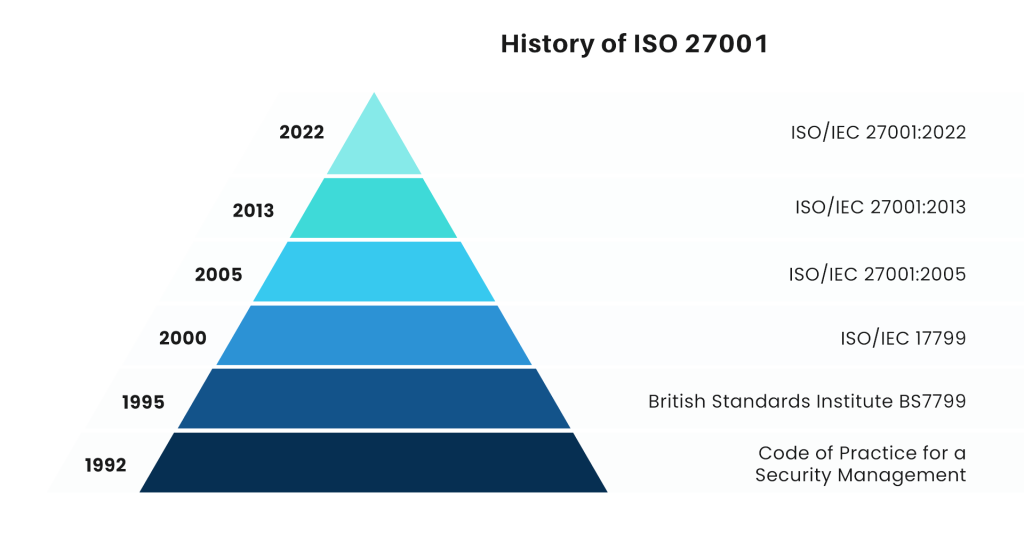
BS7799-2 is a formal standard for ISMS. This further evolved and got developed into ISO 27001 by the British Standards Institution (BSI), firstly published in 1998. ISO 27001 was first published in 2005 by the ISO (International Organization for Standardization) and the IEC (International Electrotechnical Commission).
Over the years, ISO 27001 has evolved and has adapted to new cyber threats and technological advancement. The latest version, ISO/IEC 27001:2022, is a comprehensive and globally adopted standard that reflects on current cybersecurity challenges. This version outlines security controls in Annex A while promoting continuous improvement of information security practices. This version sets a benchmark for organizations for establishing a robust information security management system.
The following structure shows the history of ISO 27001
ISO/IEC 27001: What are the Three Principles?
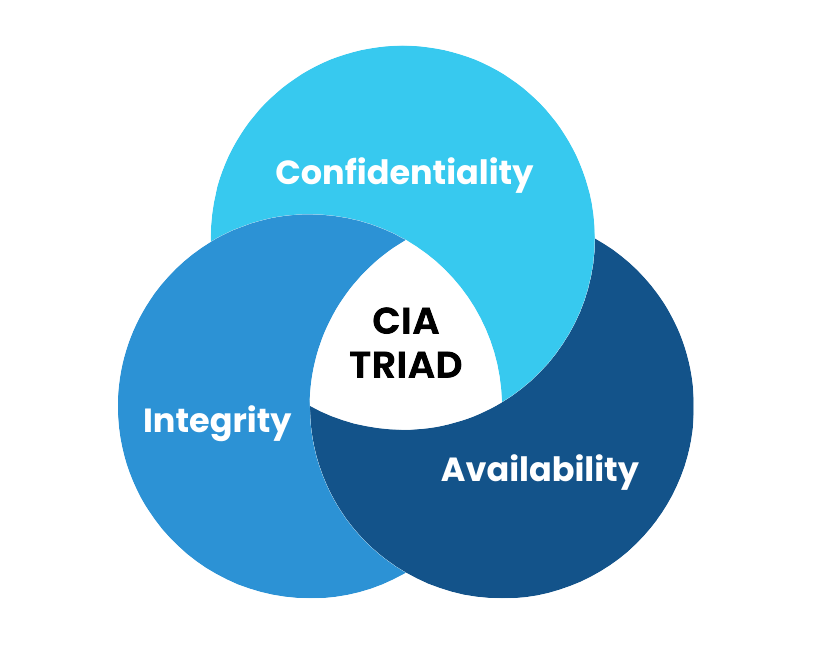
ISO/IEC 27001 is known for its globally recognized standard for information security. This standard is built on three core principles: Integrity, Confidentiality, and Availability.
Integrity: This means double-checking the accuracy and completeness of data. This standard helps in analyzing whether the data is free of errors and is kept safe in order to not be erased or damaged.
Confidentiality: Keeping data safe from unauthorized access and manipulation with the help of multifactor authentication and data encryption.
Availability: This leads to removing any bottlenecks in the security processes while minimizing vulnerabilities. It is achieved by updating software and hardware to the latest firmware. Data being available also refers to it being accessible whenever it is necessary for the business and the consumer.
With Microtek Learning, these principles are intact while protecting data from various security risks, resulting in helping organizations maintain a robust Information Security Management System (ISMS).
ISO/IEC 27001: Structure and Clauses
ISO 27001 follows a very well-structured format that helps companies to establish, implement, and maintain an effective ISMS. The structure is divided into the following clauses:
Clause 0-3: Introduction, Scope, Normative references and Terms and Definitions – The normative reference in ISO 27001 is equipped with several standards that provide focus on other aspects of information security management. This includes ISO/IEC 27000, ISO/IEC 27002, ISO/IEC 27005, ISO/IEC 27006, ISO/IEC 27007, and ISO/IEC 27008.
Clause 4: Content and Organization – This requires a core understanding of internal and external issues that will contribute to effective management of information security risk. It also would deal with the identification of stakeholders and the defining of the ISMS scope.
Clause 5: Leadership – This refers to management showing commitment towards the Information Security Management System (ISMS). It also includes some of the key steps such as defining ISMS policies, assigning relevant roles, conducting internal audits, and identifying any non-conformities.
Clause 6: Planning – Planning includes assessing risks and planning security objectives while working on achieving them.
Clause 7: Support – This cause focuses on providing necessary resources, skills, and communication for supporting ISMS. To the core, this also includes documenting the personnel, software, hardware, and other resources for information security purposes.
Clause 8: Operations – It provides planning and execution of ISMS processes while including assessment and treatment plans. An organization must focus on implementing policies and procedures in order to protect their data from threats and unauthorized access.
Clause 9: Performance Evaluation: This clause includes measuring, monitoring, and auditing the ISMS to ensure continuous improvement. This also includes internal audit and management review.
Clause 10: Improvement – The improvement clause promotes the identification of nonconformity while taking corrective actions for improving the ISMS continuously. Nonconformity could include failing to meet the standard requirements, lack in information security management system, or any other issue that might lead to a security breach in the future.
ISO/IEC 27001: Steps to Achieve Certification
With the changing landscape of data and cybersecurity, it is evidently important to learn everything about ISO 27001 for standard protection and to successfully achieve its certification. Given below is a brisk of steps that can be followed for completing the process.
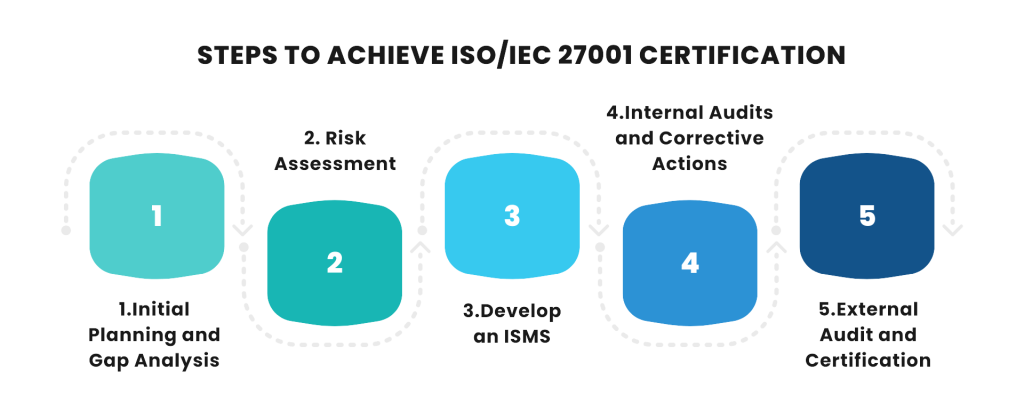
Step 1: Initial Planning and Gap Analysis
The very first step consists of assigning an ISO team that is dedicated to the certification process. This team then is responsible for defining the scope of ISMS, conducting the gap analysis, building the ISMS, and creating a statement of applicability.
Step 2: Risk Assessment
Conducting a risk assessment after the analysis of the initial stage focuses on identifying and evaluating potential security risks.
Step 3: Developing an ISMS
ISMS plays a vital role in the entire process. This step refers to creating a formal ISMS tailored for your organization that will include policies, procedures, and controls for mitigating risk.
Step 4: Internal Audits and Corrective Actions
The second-to-last step includes conducting internal audits and further undergoing Stages 1&2 of the audit. Conducting internal audits helps in identifying any areas of non-compliance while taking necessary corrective actions.
Step 5: External Audit and Certification
The final is that the organization undergoes an external audit by an accredited certification body. If your ISMS meets the standard’s requirements, you will receive the ISO/IEC 27001 certification
ISO/IEC 27001: Benefits and Advantages
Completing the above-discussed procedure and implementing the ISO/IEC 27001 in your organization has several benefits beyond compliance. Some of the key benefits include:
Enhanced Cybersecurity: This certification ensures all the angles for protecting your data from any kind of cyber threat. It directly contributes to your built system and further helps in building a solid foundation for future protection as well.
Increase Consumer Trust: With ISO 27001 certification, consumers and partners are more likely to trust companies that have demonstrated their commitment to data security.
Improved Compliance: Achieving ISO 27001 results in ensuring that the business meets regulatory requirements while reducing the risk of penalties.
Reduce Human Errors: With a structured standard of ISMS, ISO 27001 specializes in reducing human errors that can lead to threats and security issues.
Reduces Financial Loss: This certification directly contributes in reducing financial losses associated with data breaches and security & compliance issues.
ISO/IEC 27001: Implementing with Microtek Learning
Implementing ISO 27001 with Microtek Learning requires well-structured planning while clearly defining the phases for a smooth procedure.

Initial Assessment: Microtek Learning will help you assess your current security posture and identify gaps in your compliance with ISO 27001 requirements.
Planning: The next phase involves defining the ISMS’s scope, conducting risk assessments, and developing a roadmap for implementation.
Implementation: With Microtek Learning, you will get a step-by-step guide for implementing policies, controls, and procedures compliant with ISO 27001 standards.
Training: Microtek Learning provides comprehensive training to ensure your team is familiar with ISO 27001 requirements and security best practices.
Internal Audits: Conduct internal audits to verify the ISMS’s effectiveness and prepare for the certification audit.
Certification Audit: We help you to coordinate the certification process and ensure you meet all requirements to achieve ISO 27001 certification.
Conclusion
ISO/IEC 27001 is a powerful tool for any organization that aims to build and improve its cybersecurity. With the establishment of an ISMS, companies can protect their own data, manage risks, and increase consumer satisfaction. With completion of this certification, the path may seem complex, but the long-term benefit of the process will outweigh the initial effort.
By taking the right steps now, you can take control of the organization’s cybersecurity. Start your ISO/IEC 27001 journey today and protect your data from threats for future success!
FAQs
1. What is ISO/IEC 27001?
ISO/IEC 27001 is an international standard that provides guidelines for managing information security risk.
2. What is ISO/IEC certification?
ISO/IEC 27001 certification is an internationally recognized standard for information security management. It outlines best practices for the establishment, implementation, maintenance, and continual improvement of an information security management system (ISMS). This certification demonstrates that an organization must have a robust system in place for managing and protecting sensitive information.
This certification shall ensure confidentiality, integrity, and availability.
3. How do I get ISO 27001 certified?
To become ISO 27001 certified, you need to follow the given steps below:
- Understand the Standard: Familiarize yourself with the ISO/IEC 27001 standard, which focuses on Information Security Management Systems (ISMS).
- Gap Analysis: Conduct an internal audit to identify gaps in your security practices compared to the standard.
- Develop an ISMS: Create an Information Security Management System tailored to your organization’s needs, including policies, procedures, and controls.
- Implement and Monitor: Implement the ISMS and continuously monitor its effectiveness.
- Hire a Certification Body: Choose an accredited certification body to audit your ISMS.
- Pass the Audit: The certification body will evaluate your system. If it meets the requirements, you will receive ISO 27001 certification.
4. How long does it take to get ISO/IEC 27001 certified?
The timeframe depends on the size and complexity of the organization, but it is generally between a few months and a year.
5. How can ISO 27001 help an organization improve information security?
ISO 27001 helps organizations to improve information security by providing a structured framework for identifying risks, implementing security controls, and monitoring threats. Through the Information Security Management System (ISMS), companies can proactively address vulnerabilities and ensure that their security practices are pacing with the emerging threats.
6. Is ISO 27001 certification worth it?
The answer is yes; ISO 27001 certification is worth is for organizations as it shows the commitment to keeping one’s data protected and safe from emerging and existing cybercrime and threats.
7. What is the full form of ISO?
ISO stands for International Organization for Standardization
8. Is ISO 27001 mandatory?
The answer is no; ISO 27001 is not legally required.
9. How to implement ISO 27001 in an organization?
The implementation of ISO 27001 involves several steps:
- Conducting a gap analysis to assess current security practices.
- Conduct a risk assessment to identify potential security threats.
- Developing an ISMS tailored to the organization’s needs.
- Documenting security policies and procedures.
- Conduct internal audits and make the necessary improvements.
- Undergoing an external audit to obtain certification.
10. How difficult is ISO 27001 certification?
ISO 27001 certification can be challenging, but it is achievable with the proper planning and resources. The process requires a thorough understanding of the standard, time to implement an ISMS, and a commitment to continuous improvement. Working with experienced consultants and conducting internal audits can make the process smoother. Although the process can be complex, most organizations can achieve certification with the proper preparation, instilling confidence in your ability to succeed.



