
With more data being generated every second, there is no second opinion of rising threats. Threats to data are a major problem for every single company existing in today’s time with sensitive information that needs to be protected. Hacking is one of the origins that produces threats, but there is a positive side to this as well.
Ethical Hacking is known for the exposure of data with the permission of owners to identify vulnerabilities in the network. In this blog, we will dive deep into what does an ethical hacker do and explore this section of the industry, its certifications and the advantages.
Introduction: What is Ethical Hacking?
Ethical Hacking the term was first introduced in 1995 by John Patrick. He was IBM’s Vice President at that time. Ethical Hacking has been around for long enough from the start, but this was the first time this term was given a platform after decades. In fact, in the early 1960s, Hacking didn’t have such a negative notion of its name. These periods called for students to utilize this information and increase the efficiency of machines and systems.
Carrying an important position in the digital market, ethical Hacking refers to the testing of computers, networks, and applications to purposely identify loopholes in threats and security susceptibility. Its primary goal is to find loose connections between software and applications that can turn into a major issue for the corporation. This approach is significantly important for organizations as it helps to strengthen defenses and prevent cyberattacks on sensitive data.
Who is an Ethical Hacker?
An ethical hacker is a professional who is trained in procedures that help to retaliate against cyberattacks. These security experts perform security assessments with the permission of owners to gradually increase the security of sensitive data. Their skills and technical knowledge help them to stand out in understanding complex involvements of hacking a perfectly working network or application, resulting in finding threatening concerns. Maintaining the decorum of security with the owner’s permission, ethical hackers should ensure they follow certain protocols like staying legal and respecting the data’s privacy.
How is an Ethical Hacker Different?
Hacking in itself builds a negative norm in our heads, but ethical Hacking has different goals. An Ethical hacker uses all of their expertise to prevent and resolve issues that could occur due to packed or protective walls and security loopholes.
They utilize their knowledge and skills to improve the required set of networks and security regions in the software so that it is not easily penetrated by a hacker. It is more like building thick walls around a house so that the risk of getting robbed goes down. Their procedures include looking for vulnerabilities so that they can prevent security breaches and continuously contribute to building an efficient security system.
Unlike hackers who are working towards gaining financial and other aimed targets to harm the owners, ethical hackers focus on sabotaging any type of malicious authorization. Ethical hackers also indulge in working against the security system and defacing the website only to resolve the loose ends and find a perfectly working secured annotation for the organization.
Types of Ethical Hackers
There are three main categories of ethical Hacking. They are white hat hacker, black hat hacker and grey hat hacker. By neutralizing security protocols, these hackers are authorized experts to build efficient security systems and eventually help organizations avoid malicious threats and cyberattacks. Furthermore, let’s learn a little more about these three major categories.
White Hat Hacker
The term white hat hacker refers to the individual who has the authority to access sensitive information from the owner and identify points lacking in the security of the system to fight against threats.
White hat hackers are efficient in highlighting penetration concerns in the software or application, working on making it more efficient and threat-proof, all while being the rule of law.
Black Hat Hacker
Black hat hackers do not have the authority to penetrate potential websites. They are criminally responsible for threatening a fully working system, further retarding it to the point where it is damaged to a point. Also known as crackers, these hackers gain access to destroy your data or to gain financial benefits.
Their goal to harm the system through malicious actions is the reason they are known for their illegal access and potential criminal involvement. They learn these tactics either from purchasing hacker tools or previous positions. They exploit security lapses and harm the existing variety of security introduced to any type of system. Ransomware that occurred in 2018 is a great example of black hat hacking.
Grey Hat Hacker
This category of hackers involves the same individuals who have a certain significance in hacking the systems and exposing the vulnerable sides of a program, but they don’t have access to it. They primarily perform these tasks by gaining their own information without authority.
This might come into the criminal side of the term, but usually, they expose the applications to these attacks and report them to companies for improvement. To reveal the full details, grey hat hackers might demand payments in exchange for full exposure to the information they have collected.
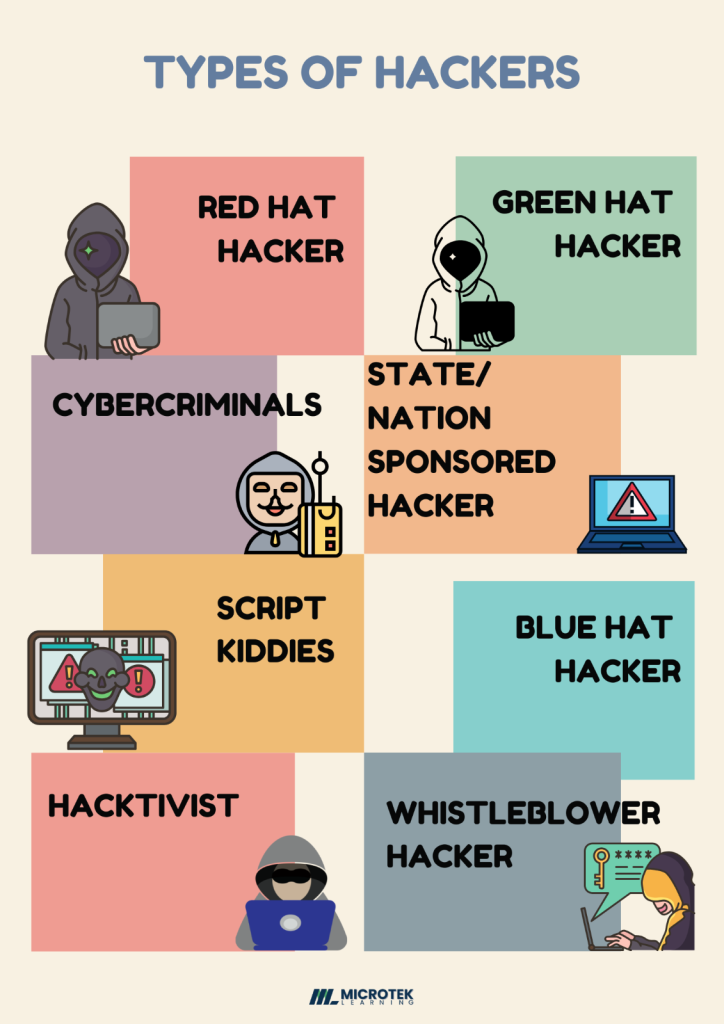
There are several other types of hackers that one should be aware of, and these are precisely mentioned in the diagram below.
Ethical Hacker: How Can You Become One?
As exciting as this position is, there is a path to be followed to create an ethical hacking career. The role of an ethical hacker consists of uncovering potential dangers that can be prevented before time with primary coverage of security concerns. Let’s dive into the steps to become an ethical hacker.
Foundational Skills
The very first step involved getting to know the basic concepts of Windows, networking and computer science. Covering this section helps one to acknowledge the important terms and topics so that one can focus on learning advanced hacking concepts and tools. Acquiring the basic knowledge of understanding systems helps in analysing them for potential vulnerabilities. This is the foremost ethical hacking skill needed by an individual looking to become a professional in the industry.
Involvement in Programming Languages
A budding hacker should master all the necessary programming languages so that he/she should be able to utilize the systems as they desire. C is one of the most demanding languages that are supposed to be known, but knowing multiple languages at the same time gives an upper hand in the process. A hacker who knows different languages is able to dissect and understand the issue from various levels, hence finding the necessary loopholes and fighting them back with better scrutiny of security. Some of the important languages one should know are Python, JavaScript, SQL and PHP.
Understand Networking Concepts
Knowing networking concepts and their vulnerabilities is a prominent ethical hacking skill. Getting well-versed in the protocol is beneficial for condemning potential threats and finding in-depth knowledge. There are various important concepts, such as server message block, DNS (domain name service), wireless networks, automobile networks, and Bluetooth networks, that one should be aware of.
Certifications
Now that you are aware of the primary steps of information, you are ready to take the next step and become certified in the domain. There are several popular certifications that you can pursue to become certified in the field. Some of them are discussed below.
1. Certified Ethical Hacker (CEH)
- Validity Duration: 3 years
- Provided by: EC-Council
- Level: Entry to Advanced Level
- Requirements:
- Two years of work experience in information security
- Or completion of official training
- Exam Details: (Knowledge Exam)
- Exam format: multiple-choice No. of Questions: 125
- Duration: 4 hours
- Passing score: 60% to 85%
- Exam Details: (Practical Exam)
- Exam format: 20 challenges
- Duration: 6 hours
- Passing score: 60% to 85%
2. Offensive Security Certified Professional (OSCP)
- Validity Duration: 3 years
- Provided by: Offensive Security (OffSec)
- Level: For Established professional
- Requirements:
- Required to have strong knowledge of systems like Linux and networking.
- Exam Details
3. CompTIA PenTest+
- Validity Duration: 3 years
- Provided by: CompTIA
- Level: Intermediate to Skilled
- Exam Details: (Code: PT0-002)
- Exam format: multiple-choice and performance-based
- No. of Questions: 85
- Duration: 165 minutes
- Passing score: 750 on a scale of 100-900
- Exam Details: (Code: PT0-003)
- Exam format: multiple-choice and performance-based
- No. of Questions: 90
- Duration: 165 minutes
- Passing score: 750 on a scale of 100-900
Job Opportunities
With the digital transformation of the world, Hacking is no longer an unknown position. While experts anticipate the growing rate of cybercrime per year by 15%, ethical Hacking is less of a job and more of a major in-demand position in the industry. Costing $10.5 trillion annually, cybercrime is one of the most expensive shifts in the economy.
Moreover, the average salary of an ethical hacker in the US stands at $1,47,087 USD. So, if you are looking for a career change or an advancement in your current position, ethical Hacking can be your next step.
Conclusion
Ethical Hacking is an interesting and impactful career. With a visible line in between of authorized Hacking and criminal involvement, this particular position in the industry has a major hold on upcoming scenarios in the IT industry.
The nature of the certification and its crucial role in any major organization is a sign of becoming an ethical hacker. It’s an exciting career path that creates a new business for the industry, which plays a vital role in the future of digital data.
Thus, if you wish to learn more about the certification and become one of the professionals, you can tap into Microtek Learning. Our professionals hold years of experience. We also provide certification in the same.



